Deploying .NET Framework Applications
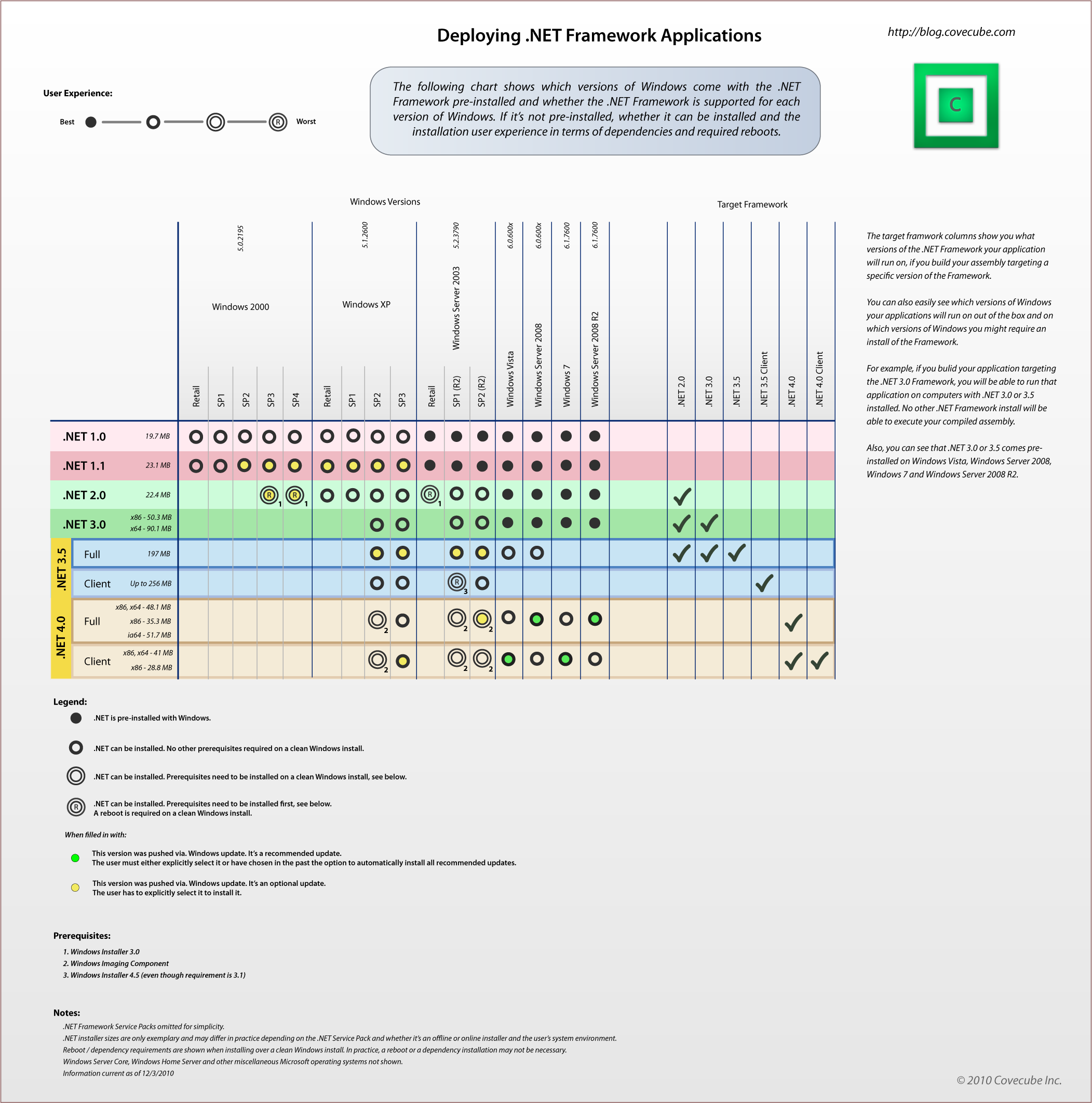
Creating .NET applications that just run on any version of Windows can be tricky. For BitFlock, the requirement was to create a Windows application that will be very easy to run. There’s no need for installing it into the user’s system and…